This page will eventually get around to examining a few ways that DEBUG can be used to study x86 Assembly Language, but first I'd like to present a little illustration which may be a bit confusing at first for some of you...
The following text is a fancy signature which I found appended to the end of a file by someone called The Bitripper. The outline drawing of TB is rather obvious, but you might be asking yourself, "What do the rows of letters and digits mean?" Well, as The Bitripper said (at the end of the last line), you should "c4urself" (See for yourself !) If you already have an idea about why The Bitripper put this (code?) here, then please go ahead and find out on your own before reading any further!
--
B013CD1033C0BFB001B9007DF3ABBAC803EE42FEC980/~~~~~~~~\ The Bitripper
FB3C730580C304EB0880FF3C730380C7048AC3EE8AC7/' `\~~~\
EE32C0EEE2E3B1C88106AC01E9628006AC01628116AE`\ /' )
011936A1AE0133D2BB4001F7F38BF2FE8C707DE2DDBE`~~/ \~~' / Coders do it
F102BFB17EB162BA3E018A9CC0FE8A44FF03D88A4401/` ) `\ bit by bit
03D88A84400103D8C1EB02881D46474A75E246464747/ / )
E2D9BEB27EBFB201B97E3E5157F3A55E6800A007BF02(_______/ /
7D59F3A51E07B401CD16748CB80300CD10C3c4urself`.____/'
--If you don't have the
slightest idea where to begin in solving the mystery of these lines, then
here are some helpful hints:
Since this signature file was created
by an "assembly coder," we'll assume that...
So, run off to your Hex editor and find out what it means...
``What's that you say? It's too much typing; there should be a better
way to do this!?'' I guess your Hex editor doesn't support importing
Hex code from an ASCII based text file!? (If you're interested in one that
does; and for free, keep reading.)
First, I'll show you a method that takes a bit longer than importing the
code directly, but it will save you from most typos and the
chances are it's already installed on your computer: MS-DEBUG (from almost
any version of MS-DOS up through WINDOWS 9x/NT or whatever). To check for
its presence: Try finding the file debug.exe
; normally found in your C:\WINDOWS\COMMAND folder (9x).
[ For those of you who do NOT have DEBUG available in a DOS-Window, you can
download a hex editor with an import function here:
Frhed: Free Hex Editor. ( You can
also click here: For info on using
DOS-Windows.)
IF you DO have access to DEBUG, I encourage you to try learning more about
it by working through the data on this page -- even those without DEBUG
should skim through this material to see if their own conclusions about the
Hex data are correct! At the end of the page I'll describe
how FRHED greatly simplifies the process of importing the hex data, if you
don't want to use DEBUG.]
OK, Let's Find Out What It Means!
Simply copy and paste the lines into a text editor such as NOTEPAD. First
remove the non-Hex characters on the right side and then the blank spaces
at the left until all the lines are flush against the left-hand margin. Now
you can see that all the lines have the same length EXCEPT for the last
one... AFTER you remove the "c4urself" they should look like
this:B013CD1033C0BFB001B9007DF3ABBAC803EE42FEC980
FB3C730580C304EB0880FF3C730380C7048AC3EE8AC7
EE32C0EEE2E3B1C88106AC01E9628006AC01628116AE
011936A1AE0133D2BB4001F7F38BF2FE8C707DE2DDBE
F102BFB17EB162BA3E018A9CC0FE8A44FF03D88A4401
03D88A84400103D8C1EB02881D46474A75E246464747
E2D9BEB27EBFB201B97E3E5157F3A55E6800A007BF02
7D59F3A51E07B401CD16748CB80300CD10C3
Now arrange all the
digits so you have only 32 of them (or 16 bytes) per line;
this will make it easier to enter the data later on! Your file should now
look like this:B013CD1033C0BFB001B9007DF3ABBAC8
03EE42FEC980FB3C730580C304EB0880
FF3C730380C7048AC3EE8AC7EE32C0EE
E2E3B1C88106AC01E9628006AC016281
16AE011936A1AE0133D2BB4001F7F38B
F2FE8C707DE2DDBEF102BFB17EB162BA
3E018A9CC0FE8A44FF03D88A440103D8
8A84400103D8C1EB02881D46474A75E2
46464747E2D9BEB27EBFB201B97E3E51
57F3A55E6800A007BF027D59F3A51E07
B401CD16748CB80300CD10C3
Unfortunately, DEBUG
requires that each byte must be separated by a blank space, so you'll
still have to punch a lot of keys ( but this is a lot easier to do AND
more accurate than entering each Hex byte
manually!):B0 13 CD 10 33 C0 BF B0 01 B9 00 7D F3 AB BA C8
03 EE 42 FE C9 80 FB 3C 73 05 80 C3 04 EB 08 80
FF 3C 73 03 80 C7 04 8A C3 EE 8A C7 EE 32 C0 EE
E2 E3 B1 C8 81 06 AC 01 E9 62 80 06 AC 01 62 81
16 AE 01 19 36 A1 AE 01 33 D2 BB 40 01 F7 F3 8B
F2 FE 8C 70 7D E2 DD BE F1 02 BF B1 7E B1 62 BA
3E 01 8A 9C C0 FE 8A 44 FF 03 D8 8A 44 01 03 D8
8A 84 40 01 03 D8 C1 EB 02 88 1D 46 47 4A 75 E2
46 46 47 47 E2 D9 BE B2 7E BF B2 01 B9 7E 3E 51
57 F3 A5 5E 68 00 A0 07 BF 02 7D 59 F3 A5 1E 07
B4 01 CD 16 74 8C B8 03 00 CD 10 C3
Were getting close now! A DEBUG
Entry command begins with an 'E,' a space and then the
first Hexadecimal memory address where the data will be entered followed
by the string of bytes to enter. If we can't find some kind of
meaningful pattern after viewing an ASCII
dump of the bytes, our next step will be to assume they
form an executable program. DEBUG can create a .COM program for us if we
enter the code beginning at Offset 0100 of the segment in
memory it assigns to us. So, we might as well enter the data beginning at
offset 100 hex and following... Now you can see that having each line
contain exactly 16 bytes makes it easier to count (and less likely for an
error to occur):
E 100 B0 13 CD 10 33 C0 BF B0 01 B9 00 7D F3 AB BA C8 E 110 03 EE 42 FE C9 80 FB 3C 73 05 80 C3 04 EB 08 80 E 120 FF 3C 73 03 80 C7 04 8A C3 EE 8A C7 EE 32 C0 EE E 130 E2 E3 B1 C8 81 06 AC 01 E9 62 80 06 AC 01 62 81 E 140 16 AE 01 19 36 A1 AE 01 33 D2 BB 40 01 F7 F3 8B E 150 F2 FE 8C 70 7D E2 DD BE F1 02 BF B1 7E B1 62 BA E 160 3E 01 8A 9C C0 FE 8A 44 FF 03 D8 8A 44 01 03 D8 E 170 8A 84 40 01 03 D8 C1 EB 02 88 1D 46 47 4A 75 E2 E 180 46 46 47 47 E2 D9 BE B2 7E BF B2 01 B9 7E 3E 51 E 190 57 F3 A5 5E 68 00 A0 07 BF 02 7D 59 F3 A5 1E 07 E 1A0 B4 01 CD 16 74 8C B8 03 00 CD 10 C3If you entered the data above into DEBUG and then used the DUMP command
....3......}.... ..B....<s....... .<s..........2.. .........b....b. ....6...3..@.... ...p}.......~.b. >......D....D... ..@........FGJu. FFGG....~....~>Q W..^h.....}Y.... ....t.......Not very meaningful... So, we assume The Bitripper is showing us a program of some kind. Finally, I've arranged our data in the form of a DEBUG SCRIPT FILE which you can use to quickly and automatically create a program with just a single DOS command! I've used DEBUG's N command to name the program FIRE.COM (you'll find out why later) and added a few more DEBUG commands at the end of the file to change the CX register ( RCX ) to AC (the file is 172 bytes long), the write ( W ) command to save the file to disk and the quit ( Q ) command to exit DEBUG. Make the necessary changes in your text editor and SAVE this file as FIRE.SCP (MAKE CERTAIN that you hit the ENTER key after 'Q' so a new line starts at the end of the file; DEBUG can't quit without this carriage return, and your DOS-window will lock-up if DEBUG can't quit!) :
N FIRE.COM E 0100 B0 13 CD 10 33 C0 BF B0 01 B9 00 7D F3 AB BA C8 E 0110 03 EE 42 FE C9 80 FB 3C 73 05 80 C3 04 EB 08 80 E 0120 FF 3C 73 03 80 C7 04 8A C3 EE 8A C7 EE 32 C0 EE E 0130 E2 E3 B1 C8 81 06 AC 01 E9 62 80 06 AC 01 62 81 E 0140 16 AE 01 19 36 A1 AE 01 33 D2 BB 40 01 F7 F3 8B E 0150 F2 FE 8C 70 7D E2 DD BE F1 02 BF B1 7E B1 62 BA E 0160 3E 01 8A 9C C0 FE 8A 44 FF 03 D8 8A 44 01 03 D8 E 0170 8A 84 40 01 03 D8 C1 EB 02 88 1D 46 47 4A 75 E2 E 0180 46 46 47 47 E2 D9 BE B2 7E BF B2 01 B9 7E 3E 51 E 0190 57 F3 A5 5E 68 00 A0 07 BF 02 7D 59 F3 A5 1E 07 E 01A0 B4 01 CD 16 74 8C B8 03 00 CD 10 C3 RCX AC W QFor those who are interested... "No! I did NOT run this program right away to see what it did; I first examined the Assembly instructions to determine if it was reasonably safe to run on my computer!" I'll show you how to do that soon...
C:\> debug < fire.scp - N FIRE.COM - E 0100 B0 13 CD 10 33 C0 BF B0 01 B9 00 7D F3 AB BA C8 - E 0110 03 EE 42 FE C9 80 FB 3C 73 05 80 C3 04 EB 08 80 - E 0120 FF 3C 73 03 80 C7 04 8A C3 EE 8A C7 EE 32 C0 EE - E 0130 E2 E3 B1 C8 81 06 AC 01 E9 62 80 06 AC 01 62 81 - E 0140 16 AE 01 19 36 A1 AE 01 33 D2 BB 40 01 F7 F3 8B - E 0150 F2 FE 8C 70 7D E2 DD BE F1 02 BF B1 7E B1 62 BA - E 0160 3E 01 8A 9C C0 FE 8A 44 FF 03 D8 8A 44 01 03 D8 - E 0170 8A 84 40 01 03 D8 C1 EB 02 88 1D 46 47 4A 75 E2 - E 0180 46 46 47 47 E2 D9 BE B2 7E BF B2 01 B9 7E 3E 51 - E 0190 57 F3 A5 5E 68 00 A0 07 BF 02 7D 59 F3 A5 1E 07 - E 01A0 B4 01 CD 16 74 8C B8 03 00 CD 10 C3 - RCX CX 0000 : AC - W Writing 000AC bytes - QYou should now find a copy of the program FIRE.COM in the same folder as the SCRIPT file. Before you go off to run the program... especially those of you who want to learn more about using DOS commands... You might like to check out this SCRIPT file for creating an Assembly listing of FIRE.COM using DEBUG again:
N FIRE.COM L <-- This Loads the named program from the hard drive! U 0100 01AB <-- Un-assemble code from 100h to 1ABh (ACh or 172 bytes). QSave this file as: FIREASM.SCP (Note: You need to run this SCRIPT in the same folder as the program or it won't know how to find it). Here's the DOS Command that will run the script AND re-direct its output to another file; which I've called FIREASM.TXT :
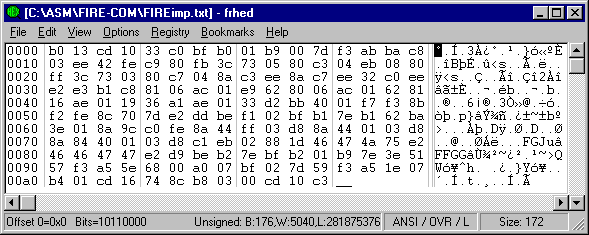
B013CD1033C0BFB001B9007DF3ABBAC803EE42FEC980 FB3C730580C304EB0880FF3C730380C7048AC3EE8AC7 EE32C0EEE2E3B1C88106AC01E9628006AC01628116AE 011936A1AE0133D2BB4001F7F38BF2FE8C707DE2DDBE F102BFB17EB162BA3E018A9CC0FE8A44FF03D88A4401 03D88A84400103D8C1EB02881D46474A75E246464747 E2D9BEB27EBFB201B97E3E5157F3A55E6800A007BF02 7D59F3A51E07B401CD16748CB80300CD10C3Now you can fire-up FRHED... Click on the File menu and choose the item "Import from hexdump..." A Dialog box will pop up allowing you to select the file containing the code. After choosing your file, you'll get a message box asking you to confirm the type of file ( Note: Later versions of Frhed may act differently than what I've shown here! ):